Controller A (Non-EEA) → Processor Z (Non-EEA) → Sub-processor Y (EEA) → Controller A (Non-EEA) (same country)
Visual
Description and Implications
-
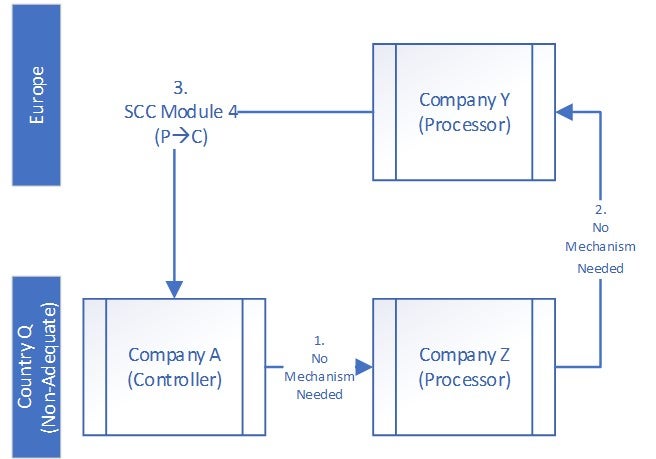
Transfer 1: No mechanism needed. Company A is not required under the GDPR to put safeguards in place to transfer information to a processor that is also located in Country Q.
-
Transfer 2: No mechanism needed. Company Z is not required under the GDPR to put in place a transfer mechanism when it transmits (exports) personal data to the EEA. Note that it is possible that the laws of Country Q independently require a transfer mechanism, however, in many jurisdictions (e.g., the United States) there is no such requirement.
-
Transfer 3: SCC Module 4. Article 46 of the GDPR requires that a processor that transfers personal data outside of the EEA to a non-adequate country must utilize a safeguard. The EDPB has confirmed that this requirement applies when an EEA processor (Company Y) sends data to a non-EEA controller (Company A).[1]
-
Subsequent Onward Transfers from Company A do not require safeguards. Note that if Company A sends data that it received from Company Y to subsequent controllers or processors it is typically not required to put a transfer mechanism in place.
-
Transfer Impact Assessments. Section 14 of SCC Module 4 does not typically require Company Y or Company A to conduct a transfer impact assessment (TIA) of the laws of Country Q. Note, however, that a TIA would be required if Company Y combined the personal data that it received from Company Z with its own personal data (e.g., did a data enhancement or a data append).
-
Law enforcement request policy. Section 15 of SCC Module 4 does not typically require that Company A takes specific steps in the event that it receives a request from a public authority for access to personal data. Note, however, that a law enforcement policy might be warranted if Company Y combined the personal data that it received from Company Z with its own personal data (e.g., did a data enhancement or a data append).
FOOTNOTES
[1] EDPB, Guidelines 05/2021 on the Interplay between the application of Article 3 and the provisions on international transfers as per Chapter V of the GDPR at para. 13.




 />i
/>i
